Professional Systems and Services
Security statement for professional systems and services
Our professional Systems* and services are core to our business and therefore security is key thereto. This document describes the general security measures we have in place for our professional systems and services. Signify may change these security measures at any time without notice so long as it maintains a comparable or better level of security.
Signify provides a wide variation of systems. Systems include web, mobile, cloud-based, on-premise, or other software applications or functionality, and/or SDKs and APIs, based on different software architectures.
We have implemented the following general security measures in our organization that apply to all our Systems. Additional specific security measures may exist within or related to Systems as each has its own considerations. For example, cloud-based systems have different security needs than on-premise systems. These specific requirements are available per system.
*Systems are our connected lighting systems, being a combination of products (hardware devices), services made available by Signify.
Our certifications: proven security standards
Signify has aligned its processes for managing the security of its Systems against the ISO 27001 international standard) and the parts of its organization related to Professional Systems and Services outside China are certified against this standard.
Signify has certified its security practices against the IEC 62443 standard, which addresses cybersecurity for operational technology in automation and control systems.
Signify has met the requirements to comply with the Spain Esquema Nacional de Seguridad (ENS) accreditation scheme at the “Medium” level. The ENS serves to establish principles and requirements for the adequate protection of information for Spanish public sector entities.
Compliance
Signify closely monitors global developments in cybersecurity. We are reviewing our products, systems, and services for compliance with applicable legal and technical requirements.
This includes obligations under new and emerging regulations such as the EU Radio Equipment Directive Delegated Act, the Cyber Resilience Act, and voluntary frameworks like the US Cyber Trust Mark.
Governance: How we organize security
Signify maintains and develops its security program and capabilities, responding and adapting to industry trends and new and emerging security threats. We regularly test and monitor the effectiveness of our safeguards, controls, and processes. Our security controls related to the delivery of our systems are regularly audited by either our internal auditor or by an independent third-party auditor.
All our employees undergo security awareness trainings. Security architects and development engineers receive in-depth training and certification. A network of security architects and security champions embedded in the development teams supports security activities related to product development.
Employees in key roles hold various industry certifications, such as Certified Information Systems Security Professional (CISSP), Certified Secure Software Lifecycle Professional (CSSLP), Certified Information Security Manager (CISM), Certified Information Systems Auditor (CISA), and Certified Ethical Hacker (CEH).
As part of its commitment to security, Signify participates in standardization bodies such as IEC, ANSI, CENELEC, CSA, and the US Cyber Trust Mark.
For more information on what we do at company level on security, please refer to the Signify Product Security Page.
The security development lifecyle: security at the heart of every phase
We have implemented security measures in accordance with our certifications during every phase of development and operations.
How Signify handles security during development
In accordance with the SDL, Signify takes the following actions during design, development, and testing:
- A security risk analysis is performed for every new development project and for every significant change to an existing system or development project.
- Automated code analysis and manual code reviews are regularly performed during development.
- Third-party code, including open-source code, is analyzed to identify and mitigate vulnerabilities.
- Hardening of the operating system and applications is performed for products, devices, and cloud-based solutions.
- Appropriate network security and firewall rules are implemented and reviewed regularly.
- Encryption of data in transit and at rest is implemented in accordance with generally accepted best-practices.
- Penetration tests are performed before each major commercial release of a system.
How Signify handles security during operations
After secure development, our systems are commercially released, and the operations phase starts. During operations we take the following measures.
Global software operations
Our cloud-based systems are managed by a specialized global operations team to ensure proper segregation of duties and least access principles.
Access rights to information
Multiple authorization levels are used when granting access to the data in the system. When a Signify employee leaves the company or move to a different role, their access rights are reviewed and revoked if needed.
Segregation of duties and least privilege access principle
We have defined authorization profiles in accordance with least privilege and segregation of duties principles and restrict and control the allocation and usage of privileged access rights.
Our employees and subcontractors are granted access only to those parts of the system needed to perform the tasks associated with their role in operating the system. Development and operations are managed within separated environment and separated teams.
Password policy
A password policy and technical controls are in place in our systems and internally within Signify that prohibits the sharing of passwords, governs responses to password disclosures, requires default passwords to be altered, and requires users to change passwords on a regular basis.
Encryption
All systems that manage customer data use encryption by applying the following measures:
- Cryptographically secure random number generation
- Crypto functions designed for expected product lifetime
- Sensitive data at rest and transit encrypted with generally accepted industry standards
Operations security
Signify has:
- Defined logically separated development, testing, and production environments
- Implemented detection, prevention, and recovery controls to protect against malicious or unauthorized access
- Defined and established roles and responsibilities associated with technical vulnerability management, including vulnerability monitoring, vulnerability risk assessment, patching, asset tracking, and any coordination responsibilities required. Depending on how urgently a technical vulnerability needs to be addressed, the action taken is carried out by following our maintenance or information security incident response procedures.
- Protected the infrastructure used for the operations of system by ensuring that all systems, networks, and supporting infrastructure are compliant to our security requirements and according to industry standard benchmarks. This includes removing or disabling unused networking and other computing services and installing various levels of system firewalls, changing all default account names and/or default passwords, and that the appropriate technical measures are in place (for example, anti-malware, logging).
- Identified and keeps an updated inventory of assets
- Implemented a rigorous process for distribution of keys and secrets
- Designed operational redundancy in our system on a risk basis
Security reviews
We perform technical security reviews such as penetration testing, vulnerability assessments, configuration reviews, application testing and code reviews. Such reviews shall not impact our customers’ business processes. We review our procedures on a yearly basis.
Device security
For the security of products, we apply the following best practices (but not limited to):
- Remove hardware debug interfaces
- Implement mechanisms designed to execute trusted code.
- Restrict communications with external interfaces
- Enforce verification of authenticity to protect firmware updates
- Provide unique device identity and certificates
- Extended Zigbee protocol with enhanced security features
Supply chain and manufacturing
Supply chain security is integral to our security processes. Suppliers undergo a risk-based security assessment and, if the supplier manages our data, an information security audit. Our processes also regulate the distribution of keys and secrets, and the controlled distribution of firmware and updates for our products during manufacturing and update.
Business continuity
We have deployed processes and technical solutions to guarantee a high level of resilience for our systems. We apply the following best practices:
- Deployment of critical systems in geographically separated data centers
- A rigorous protocol for deploying updates to cloud-based systems, which defines a formal test, development, and acceptance process prior to approving systems for production. Updates for critical security patches follow security incident response procedures.
- Our systems are designed to work without being connected to our central cloud for a period of time (system dependent).
- Protection of data in the system against loss by regularly making and testing backup copies of information, data, and system images. We protect backed-up data with even a higher level of security to address ransomware risks.
How Signify acts when there is an incident

Figure 1: Incident Management Flow
At Signify, we address security as an integral part of our quality process. Assigned responsibilities and established procedures aim at providing an adequate response to suspected security events and incidents. We have implemented and deployed a thorough process for incident management, including the creation of an Incident Response Team with members from the Business Unit, Corporate Security, Legal, and Public Relations.
Step 1: Assess the incident Each suspected security event is assessed against a set of criteria to determine whether it qualifies as a security incident.
Step 2: Check for personal data
Any actual or suspected security incident will be checked whether it involves Personal Data will be handled in accordance with our Data Processing Agreement.
Step 3: Notify our customers (customers notify us)
In case of a personal data breach on Signify side, we will notify our customers without undue delay, in accordance to our Data Processing Agreement. As in many situations the customer will be the controller of the personal data involved, it likely will be end-responsible for determination of risk and impact to rights and freedoms of individuals, and the decision on reportability.
If any incident is noted at Customer side which requires cooperation from Signify, customer should inform Signify without undue delay. Security incidents which customer becomes aware of, should be immediately communicated to our Customer Satisfaction Team, Signify’ s CERT (mail to: cert@signify.com) and the Central Privacy Office privacy.lighting@signify.com).
Step 4: Provide information flow
We will provide details relating to the security incident that has occurred, and provide customers with an overview of the systems affected by the security incident. This information may be provided in phases if not immediately available.
Step 5: Assign a direct point of contact
Our customers will be assigned a direct point of contact towards Signify if there is a security incident.
Step 6: Cooperate and solve
In some situations, we may require our customers to cooperate with us and share information. If required, we will implement a remedy and make available security advisories for our systems.
Step 7: Evaluate
Lessons-learned activities are conducted periodically to improve security measures and the incident handling process. We will perform a root cause analysis according to the that we have defined.
What Signify does when learning of a vulnerability
Signify supports coordinated vulnerability disclosure and encourages responsible vulnerability testing by security researchers and customers, with responsible reporting to Signify. Vulnerabilities are handled in accordance with our vulnerability disclosure procedure .
If required, we will make available security advisories.
Customer responsibility: solving problems together
Signify recognizes that the security of our products and services is an important part of our customers’ in-depth security strategy. Signify can secure its development and operations, but our products, services and systems also run in our customers’ environments.
Appropriate evaluation of risks and proper care during the entire lifecycle of the product—from development, to installation, maintenance, operations, and de-commissioning—are essential for mitigating internal and external threats.
Cooperation in addressing security is essential and Signify shares with our customers the responsibilities to mitigate internal and external threats to the security of our products, services, and systems.
Cloud and on-premise systems
Signify offers systems that are generally comprised of cloud components and on-premise components. Systems with cloud components are referred to as cloud systems. Cloud systems usually also have some on-premise components. Systems with no cloud components are referred to as on-premise systems.
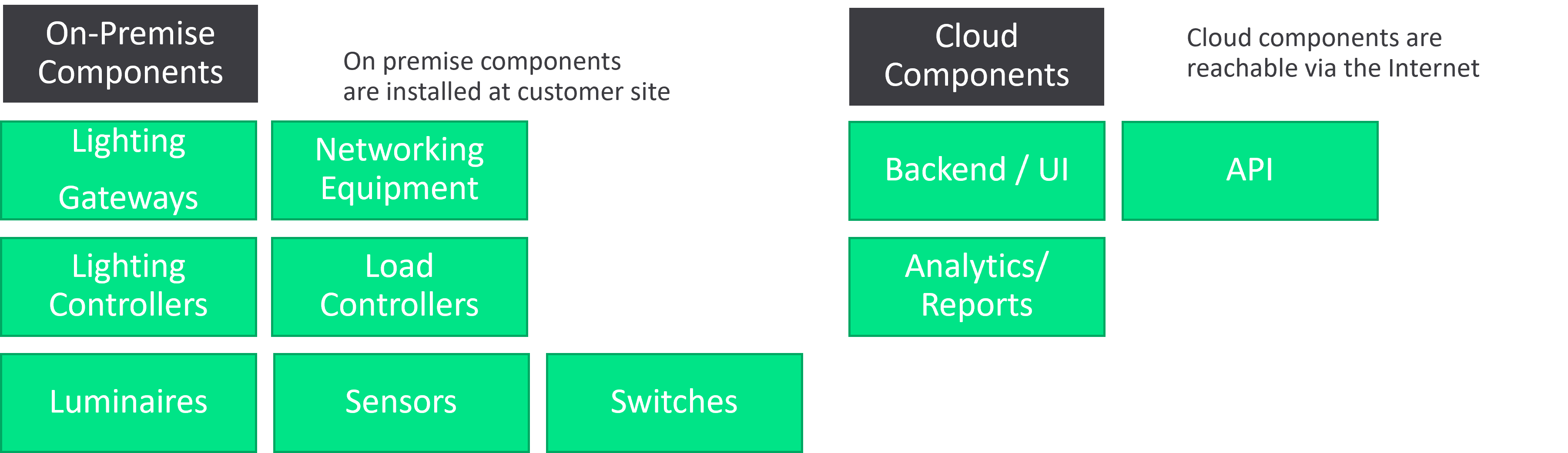
Figure 2: typical Signify Lighting System with on premise and cloud components
Signify shared responsibility model
Signify works with a shared responsibility model. The model makes clear what are Signify’s responsibilities and what are customer responsibilities. Separate product-specific security statements provide details on what Signify require customers to do for specific products and systems.
Signify operates, manages, and controls the cloud components of the system (see Figure 1). Generally speaking, Signify is responsible for the security and management of the system’s cloud components, while customers are responsible for the security and management of the system components installed on-premise.
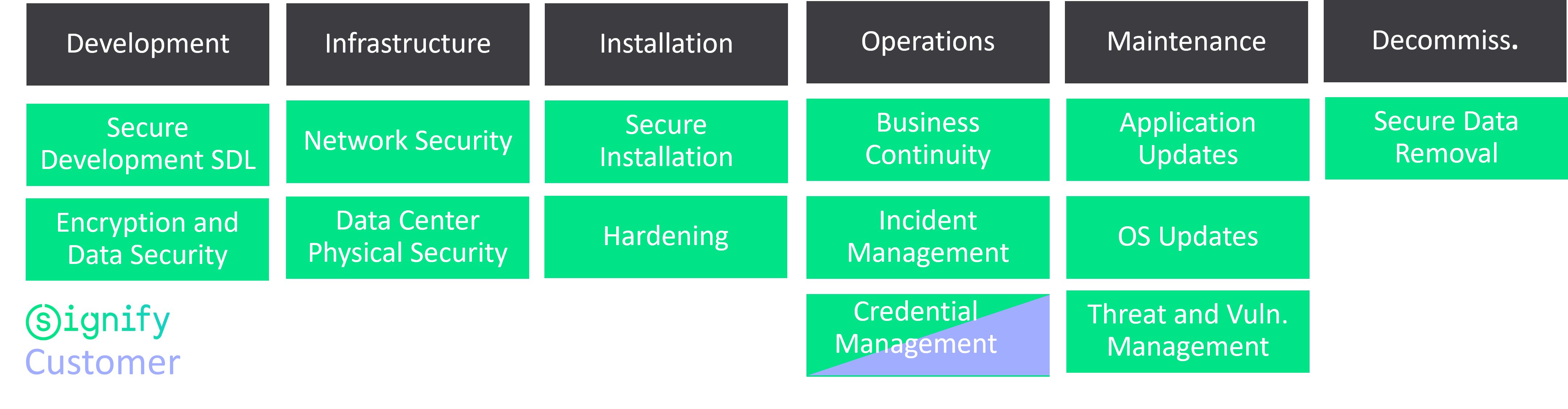
Figure 3: Responsibilities for Cloud Components (green for Signify, Blue for Customer)
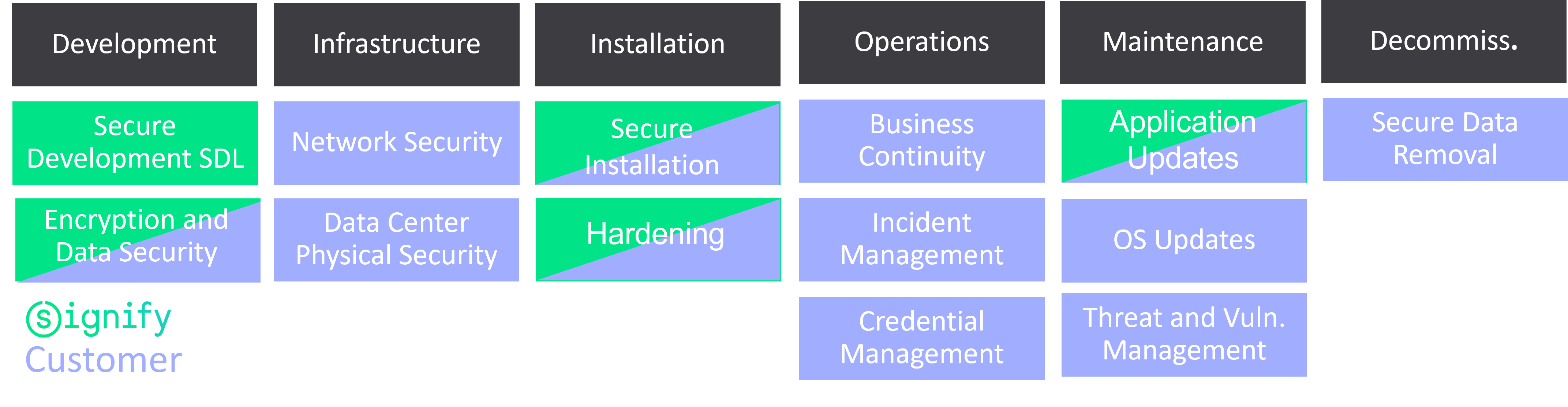
Figure 4: Responsibilities for On-Premise Components
In general, Signify is responsible for the Secure Development of both cloud and on-premise components
Customer responsibility is determined by the type of lighting systems and lighting system components that are installed. For on-premise systems, the customer is fully responsible for every aspect of the secure installation, operations, credentials management, incident management, and business continuity and maintenance of these systems. For cloud systems, the customer is responsible for the security of the on-premise components and the security of certain aspects of operations, such as credentials management.
Some activities such as Encryption and Data Security are a shared responsibility. Technologies for Encryption and data Security are responsibility of Signify, while customers Are required to manage securely their data and credentials for access to data in databases and other repositories. Detailed requirements with respect to this point are defined in the product-specific security statements.
In cases where Signify installs and commissions a system on behalf of the customer, Signify also assumes the responsibilities of the secure installation activities.